Domain Controller Certificates are a critical component of Active Directory security, ensuring the integrity and availability of domain controllers. They’re more than just a digital signature; they represent a verifiable chain of trust, protecting the entire domain infrastructure. Understanding the nuances of these certificates and how they’re generated is vital for administrators and security professionals. This article will delve into the specifics of Domain Controller Certificate Templates, covering their purpose, creation, validation, and best practices. Let’s explore how these certificates safeguard your Active Directory environment.
The rise of cloud-based Active Directory and the increasing complexity of network infrastructure have significantly increased the importance of robust security measures. Domain Controllers, the central hubs of a domain, are prime targets for attackers. A compromised Domain Controller can lead to a complete domain outage, impacting all services and applications dependent on it. Therefore, the Domain Controller Certificate Template is a cornerstone of this protection. It’s a digital signature that confirms the authenticity and integrity of the domain controller, providing a strong layer of defense against malicious actors. Without a properly validated certificate, the domain controller’s integrity is compromised, potentially leading to data loss and system instability. The template itself is a standardized format, ensuring interoperability and facilitating consistent validation across different Active Directory environments.
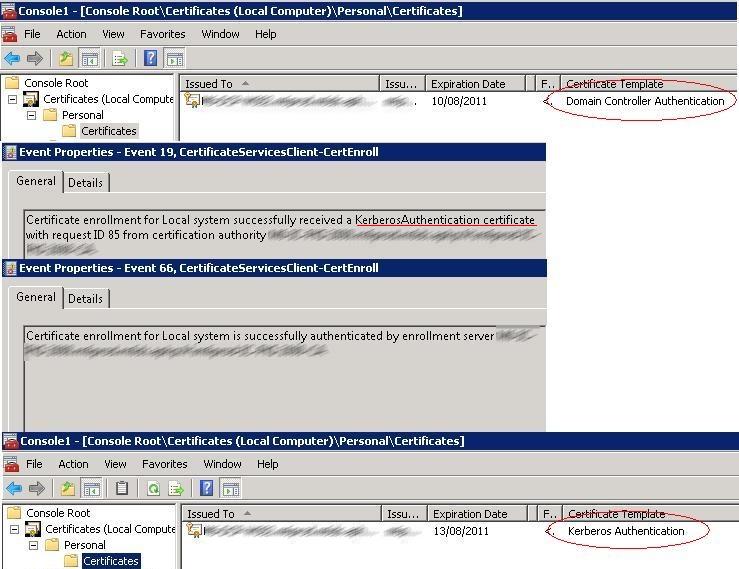
The primary purpose of a Domain Controller Certificate Template is to establish a verifiable chain of trust. It’s a digital signature that, when verified, confirms that the domain controller is legitimate and hasn’t been tampered with. This is achieved through a complex cryptographic process involving a private key and a public key. The certificate is issued by a trusted Certificate Authority (CA), providing a level of assurance that the certificate is genuine and hasn’t been forged. This is a fundamental aspect of Active Directory security, ensuring that only authorized administrators can manage the domain controller. The template itself is a standardized format, ensuring interoperability and facilitating consistent validation across different Active Directory environments. Different CA’s may issue certificates with varying levels of validation, so understanding the specific CA is important.
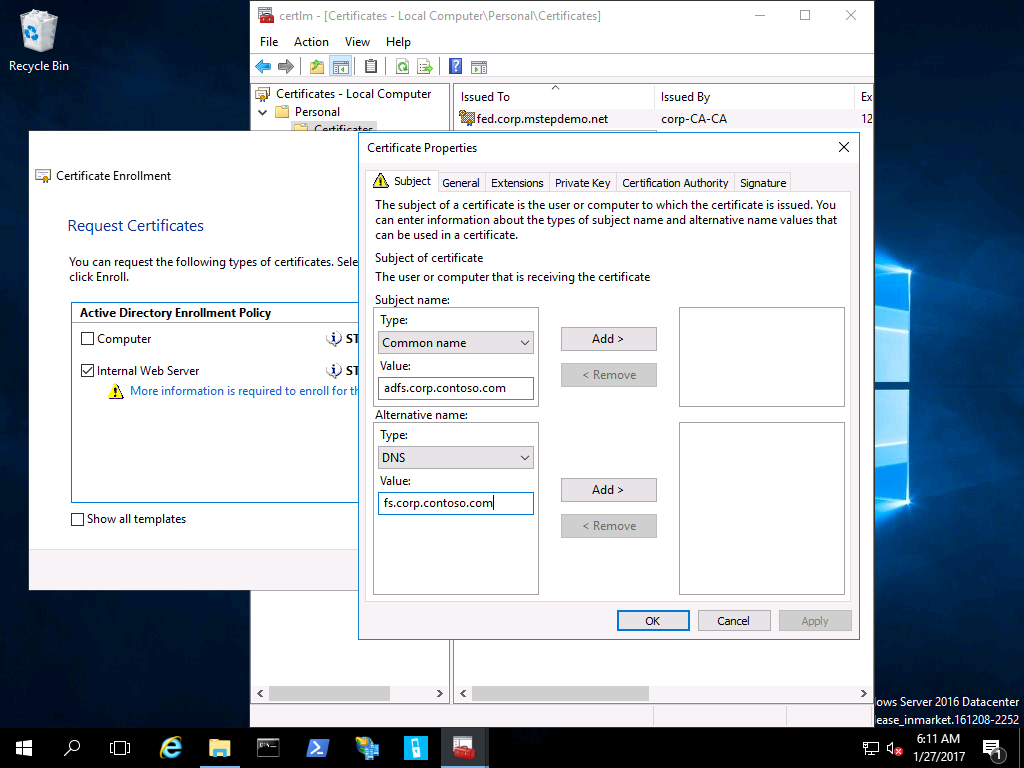
The creation of a Domain Controller Certificate Template typically involves several key steps. It begins with the domain controller itself, which is configured to generate the certificate. The certificate is then signed by a trusted CA, which verifies the domain controller’s identity and ensures the validity of the certificate. This process is automated through Group Policy, allowing administrators to easily manage certificate issuance. The template itself is a standardized format, ensuring interoperability and facilitating consistent validation across different Active Directory environments. The CA’s role is crucial here – they ensure the certificate’s authenticity and integrity. Proper configuration and monitoring of the certificate issuance process are essential for maintaining a secure domain environment.
A Domain Controller Certificate Template is more than just a digital signature; it’s a complex structure containing several critical elements. The most important component is the Private Key – this is the secret key used to sign the certificate. The certificate also includes a Public Key, which is used to verify the signature. The template also includes information about the domain controller’s Name ID, which identifies the specific domain controller being certified. Furthermore, the template includes a Certificate Validity Period, which specifies how long the certificate is valid. Understanding these components is crucial for administrators to properly manage and monitor the certificate lifecycle. The template is a standardized format, ensuring interoperability and facilitating consistent validation across different Active Directory environments.

The Certificate Validity Period is a critical parameter that determines how long a Domain Controller Certificate Template is valid. This period is typically set to a shorter duration, such as 90 days, to minimize the risk of compromise. A shorter validity period reduces the potential impact of a compromised certificate, as it will expire sooner. However, it’s important to balance this with the need for sufficient security. Administrators must carefully consider the risk tolerance of their environment when setting the validity period. A shorter validity period is generally recommended for environments with a higher risk profile, while longer validity periods may be acceptable for less critical environments. Regularly reviewing and adjusting the validity period is a best practice.
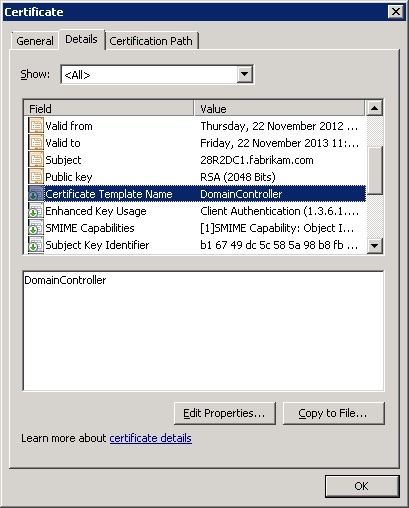
Validating a Domain Controller Certificate Template is a vital step in ensuring the security of your Active Directory environment. There are several methods available for validating certificates, including:

The choice of validation method depends on the specific requirements of the environment. A layered approach, combining multiple validation methods, is generally recommended for enhanced security. Automated certificate validation tools can significantly streamline this process, reducing the risk of human error.
Effective management of Domain Controller Certificates is essential for maintaining a secure and reliable Active Directory environment. Here are some best practices:
The lifecycle of a Domain Controller Certificate Template is a critical aspect of its management. It’s not just about issuing the certificate; it’s about maintaining its validity and ensuring its security. This involves several stages:
Understanding and adhering to this lifecycle is crucial for maintaining a secure and reliable Active Directory environment. Failure to properly manage the certificate lifecycle can lead to significant security vulnerabilities.

Domain Controller Certificate Templates are a fundamental security component of Active Directory environments. They provide a verifiable chain of trust, protecting the integrity and availability of domain controllers. Proper management of these certificates, including regular audits, automated renewal processes, and robust key management practices, is essential for maintaining a secure and reliable environment. As Active Directory continues to evolve, the importance of these templates will only continue to grow. By understanding the purpose, creation, validation, and lifecycle of these certificates, administrators can effectively safeguard their domain infrastructure and mitigate the risks associated with compromised domain controllers. Investing in robust certificate management practices is an investment in the long-term security of your Active Directory environment.