The escalating threat landscape demands robust security measures. Organizations of all sizes are increasingly reliant on comprehensive information security reports to demonstrate due diligence, identify vulnerabilities, and proactively address potential risks. A well-structured Information Security Report Template provides a standardized framework for capturing critical data, analyzing security incidents, and communicating findings effectively. This article will delve into the essential components of a robust template, offering practical guidance for creating a report that truly informs and protects your organization. Information Security Report Template is more than just a document; it’s a strategic tool for maintaining a strong security posture. It’s a vital component of compliance, risk management, and overall business continuity. Understanding the nuances of this template is crucial for anyone responsible for safeguarding sensitive data and systems.
The primary purpose of an Information Security Report Template is to systematically document security incidents, vulnerabilities, and operational controls. It’s a centralized repository of information that facilitates analysis, reporting, and continuous improvement. A clear and concise report allows stakeholders – including management, legal teams, and IT personnel – to quickly understand the current security landscape and make informed decisions. Without a standardized approach, security efforts can become fragmented and inefficient, hindering proactive threat detection and response. Furthermore, a well-crafted report demonstrates a commitment to security best practices and can be a key factor in securing funding and maintaining regulatory compliance. The template ensures consistency in reporting, promoting a shared understanding of security risks across the organization.

Let’s examine the key sections typically included in an Information Security Report Template. Each section is designed to gather specific data and insights.
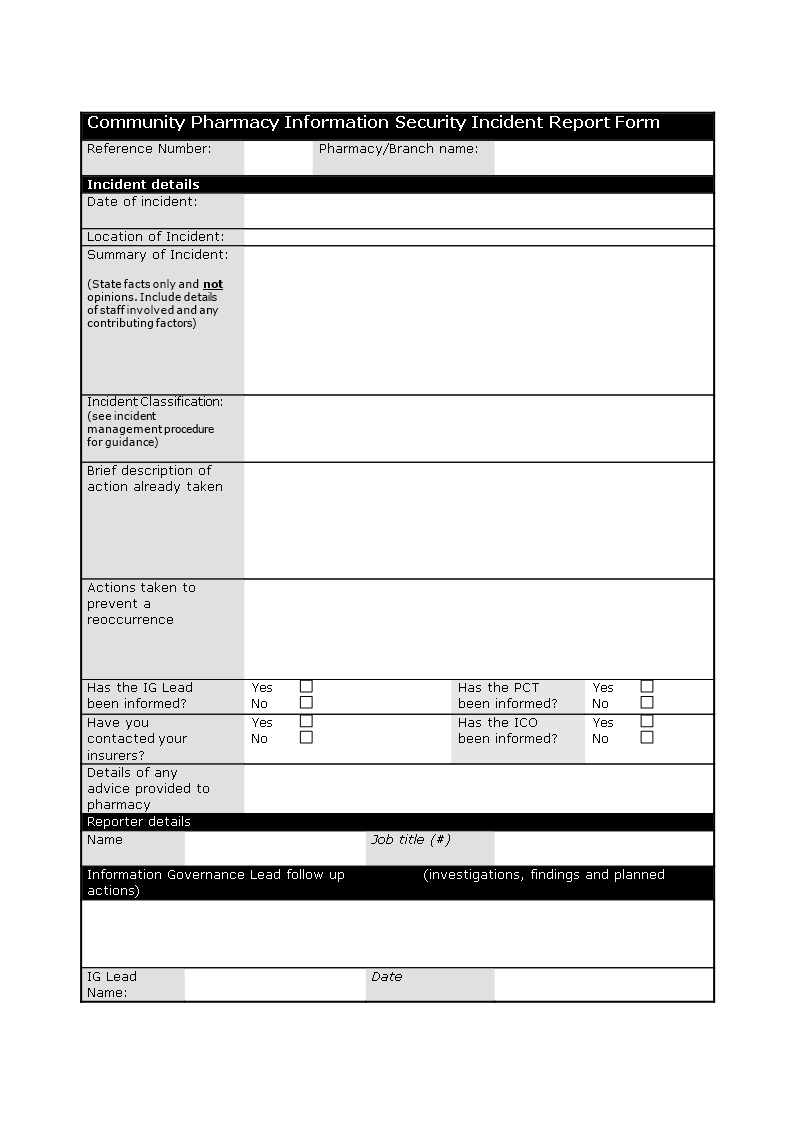
The Executive Summary is arguably the most important section of the report. It provides a high-level overview of the security situation, highlighting key findings, risks, and recommendations. It’s typically written for senior management and should be concise, impactful, and easily digestible. This section should clearly articulate the overall security posture and any significant vulnerabilities identified. Information Security Report Template emphasizes the need for a succinct and impactful summary. A strong Executive Summary sets the stage for the rest of the report.
This section details all security incidents that occurred during the reporting period. It includes information such as the date and time of the incident, the type of incident (e.g., phishing, malware infection, data breach), the affected systems, and the actions taken to mitigate the incident. A detailed log is essential for tracking trends and identifying patterns. Proper incident logging is a cornerstone of effective security monitoring. The format should be consistent and easily searchable.
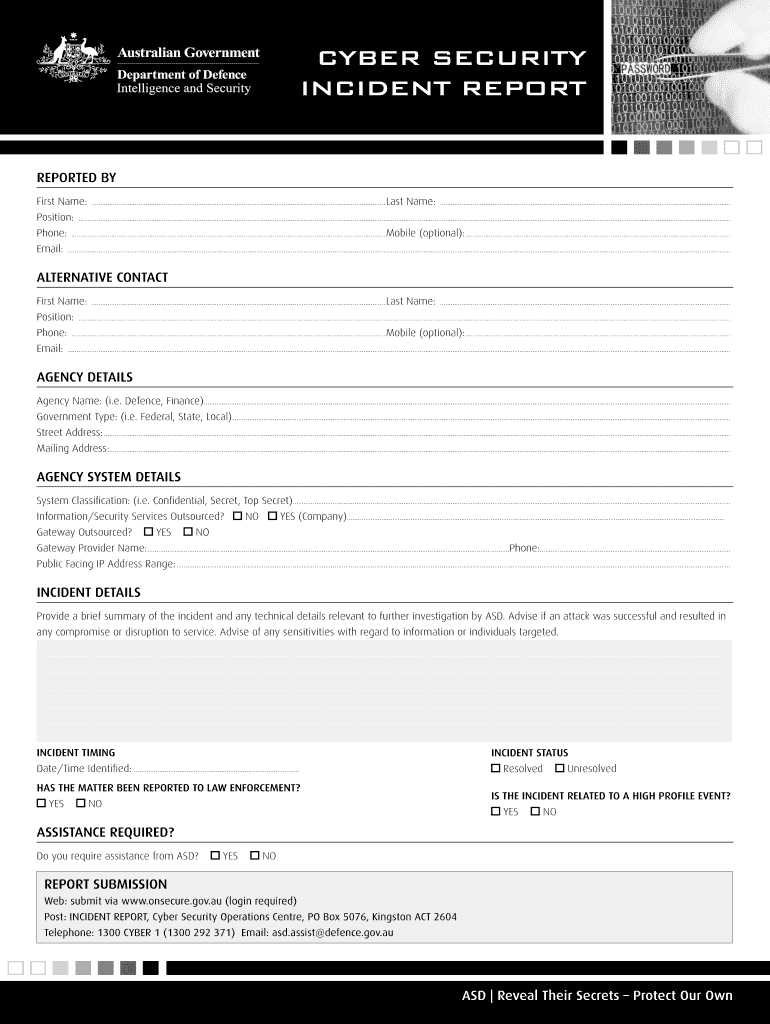
This section focuses on identifying vulnerabilities within the organization’s systems and infrastructure. It includes a review of security assessments, penetration testing results, and vulnerability scans. The report should categorize vulnerabilities by severity (e.g., critical, high, medium, low) and prioritize remediation efforts based on risk. Information Security Report Template highlights the importance of regular vulnerability assessments as a proactive security measure.

This section evaluates the effectiveness of existing security controls, such as firewalls, intrusion detection systems, antivirus software, and access controls. It assesses whether these controls are properly configured, maintained, and regularly tested. A thorough assessment of control effectiveness is crucial for determining whether current security measures are adequate to protect against identified threats. This section often includes a comparison of controls against industry best practices.
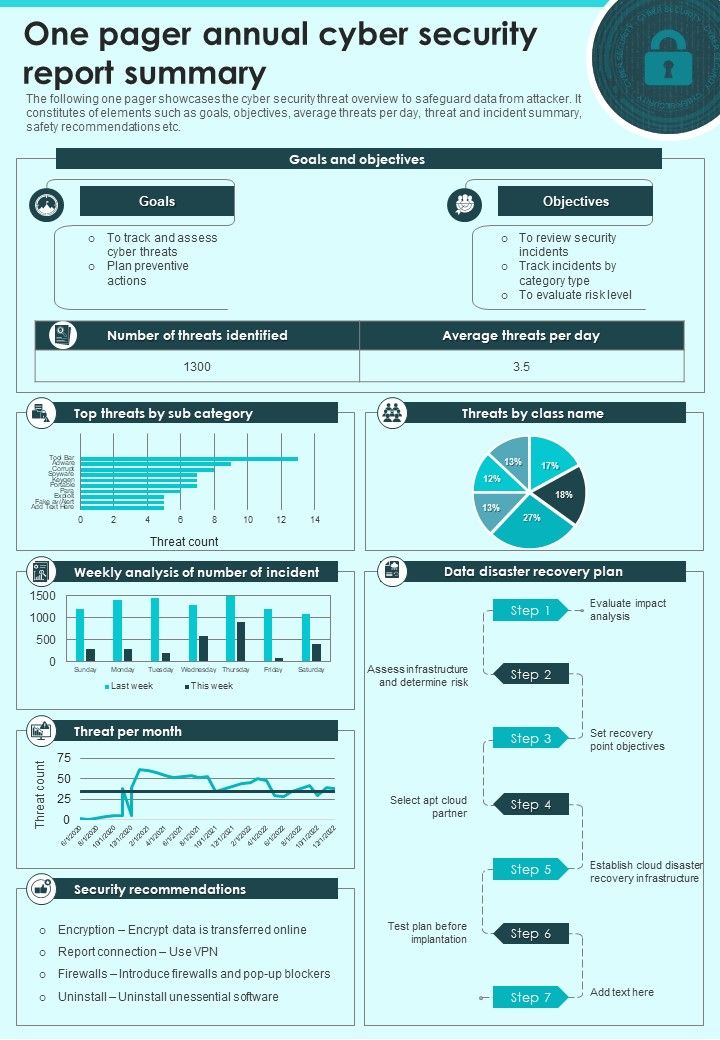
This section documents the organization’s compliance with relevant regulations and standards, such as GDPR, HIPAA, PCI DSS, and ISO 27001. It includes information on audit results, compliance assessments, and any identified gaps in compliance. Maintaining compliance is a critical requirement for many organizations, and a clear report demonstrates a commitment to meeting regulatory obligations. The report should clearly state the status of compliance and outline the steps being taken to address any gaps.

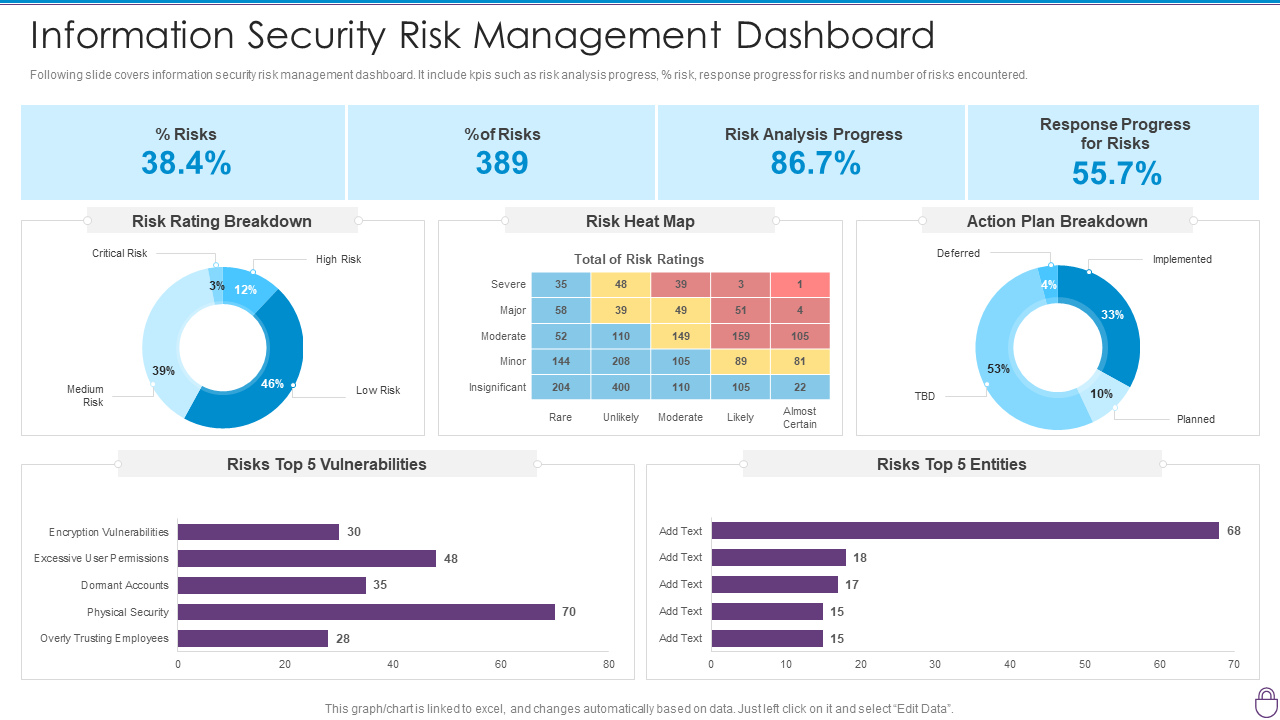
This section analyzes the potential risks posed by security incidents and vulnerabilities. It identifies the likelihood and impact of potential threats, considering factors such as the threat landscape, the organization’s assets, and existing security controls. Risk assessments help prioritize security investments and allocate resources effectively. A robust risk assessment is fundamental to informed decision-making.
This section outlines the planned actions to address identified vulnerabilities and security weaknesses. It includes specific tasks, timelines, and responsible parties for remediation efforts. A well-defined remediation plan demonstrates a proactive approach to security and ensures that vulnerabilities are addressed in a timely manner. The plan should be documented and tracked to ensure accountability.
This section includes supporting documentation, such as scan reports, vulnerability scan results, configuration files, and test results. It provides additional detail to support the findings presented in the report. Properly formatted appendices enhance the credibility and usefulness of the report.
An Information Security Report Template is a powerful tool for enhancing security awareness, improving risk management, and demonstrating compliance. By systematically documenting security incidents, vulnerabilities, and control effectiveness, organizations can gain valuable insights into their security posture and proactively address potential threats. The template provides a structured framework for collecting and analyzing data, facilitating informed decision-making, and ultimately protecting valuable assets. Ultimately, a well-executed Information Security Report Template is an investment in the organization’s long-term security and resilience. Continuous refinement and adaptation of the template to reflect evolving threats and organizational needs are essential for maintaining its effectiveness.
In today’s complex threat landscape, a comprehensive Information Security Report Template is no longer a luxury but a necessity. It’s a critical tool for organizations of all sizes to understand their security posture, identify vulnerabilities, and proactively mitigate risks. By consistently utilizing this template and adapting it to specific organizational needs, organizations can significantly strengthen their defenses and safeguard their valuable assets. The ongoing evolution of security threats necessitates a dynamic approach to reporting, ensuring that the template remains relevant and effective in the face of constant change. Investing in a robust and well-maintained Information Security Report Template is an investment in the future of the organization.
